One of the commonly asked questions from our users is how to add
another IP address to their server. You can assign your own private IP
address to your droplet by creating a VPN tunnel. Whether you want to
build your own Virtual Private Network (VPN), or assign an SSL
certificate to that IP address, you have several options. From all of
the possible options, the most optimal ones are between PPTP and
OpenVPN. A Point-To-Point Tunneling Protocol (PPTP) allows you to
implement your own VPN very quickly, and is compatible with most mobile
devices. Even though PPTP is less secure than OpenVPN, it is also
faster and uses less CPU resources.
On CentOS 6 x64:
Next, you should setup authentication for PPTP by adding users and passwords. Simply add them to /etc/ppp/chap-secrets :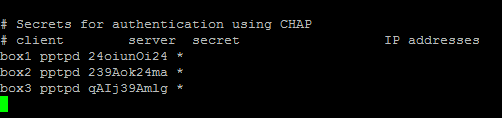 Where client is the username, server is type of service – pptpd for
our example, secret is the password, and IP addresses specifies which IP
address may authenticate.
By setting ‘*’ in IP addresses field, you specify that you would accept
username/password pair for any IP.
Where client is the username, server is type of service – pptpd for
our example, secret is the password, and IP addresses specifies which IP
address may authenticate.
By setting ‘*’ in IP addresses field, you specify that you would accept
username/password pair for any IP.
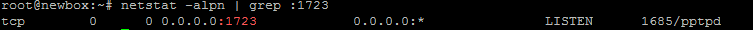
If you would like to restrict which servers can connect to your droplets, you can setup an iptables rule that restricts TCP connects to port 1723.
Step 1 - PPTP Installation
You will have to select one server to be responsible for handling out IPs to others and authenticating all of your servers into your VPN. This will become your PPTP Server.On CentOS 6 x64:
rpm -i http://poptop.sourceforge.net/yum/stable/rhel6/pptp-release-current.noarch.rpm yum -y install pptpdOn Ubuntu 12.10 x64:
apt-get install pptpdNow you should edit /etc/pptpd.conf and add the following lines:
localip 10.0.0.1 remoteip 10.0.0.100-200Where localip is IP address of your server and remoteip are IPs that will be assigned to clients that connect to it.
Next, you should setup authentication for PPTP by adding users and passwords. Simply add them to /etc/ppp/chap-secrets :
 Where client is the username, server is type of service – pptpd for
our example, secret is the password, and IP addresses specifies which IP
address may authenticate.
By setting ‘*’ in IP addresses field, you specify that you would accept
username/password pair for any IP.
Where client is the username, server is type of service – pptpd for
our example, secret is the password, and IP addresses specifies which IP
address may authenticate.
By setting ‘*’ in IP addresses field, you specify that you would accept
username/password pair for any IP.Step 2 - Add DNS servers to /etc/ppp/pptpd-options
ms-dns 8.8.8.8 ms-dns 8.8.4.4Now you can start PPTP daemon:
service pptpd restartVerify that it is running and accepting connections:
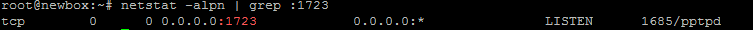
Step 3 - Setup Forwarding
It is important to enable IP forwarding on your PPTP server. This will allow you to forward packets between public IP and private IPs that you setup with PPTP. Simply edit /etc/sysctl.conf and add the following line if it doesn’t exist there already:net.ipv4.ip_forward = 1To make changes active, run sysctl -p
Step 4 - Create a NAT rule for iptables
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE && iptables-saveIf you would also like your PPTP clients to talk to each other, add the following iptables rules:
iptables --table nat --append POSTROUTING --out-interface ppp0 -j MASQUERADE iptables -I INPUT -s 10.0.0.0/8 -i ppp0 -j ACCEPT iptables --append FORWARD --in-interface eth0 -j ACCEPTNow your PPTP server also acts as a router.
If you would like to restrict which servers can connect to your droplets, you can setup an iptables rule that restricts TCP connects to port 1723.
